Introduction: When Military Meets Civilian Protection
The principles that protect military fortresses have found a crucial new application in civilian nuclear facilities, creating some of the world’s most secure industrial structures 1. Nuclear power plants represent critical infrastructure that requires exceptional protection against both conventional threats and evolving challenges in our modern world 23.
As nuclear energy continues to play a vital role in many nations’ power portfolios, the importance of hardening these facilities against potential threats has become increasingly important 2. These protection strategies employ a sophisticated multi-layered approach borrowed directly from military defense doctrines 4.
The concept of “nuclear facility hardening” encompasses all physical and operational measures implemented to protect nuclear materials and infrastructure from unauthorized access, sabotage, theft, and natural disasters 3. This comprehensive approach creates facilities that function effectively as both power generators and fortresses 56.
Defense-in-Depth Layers in Nuclear Facility Security
The Evolution of Nuclear Security: From Safety to Hardening
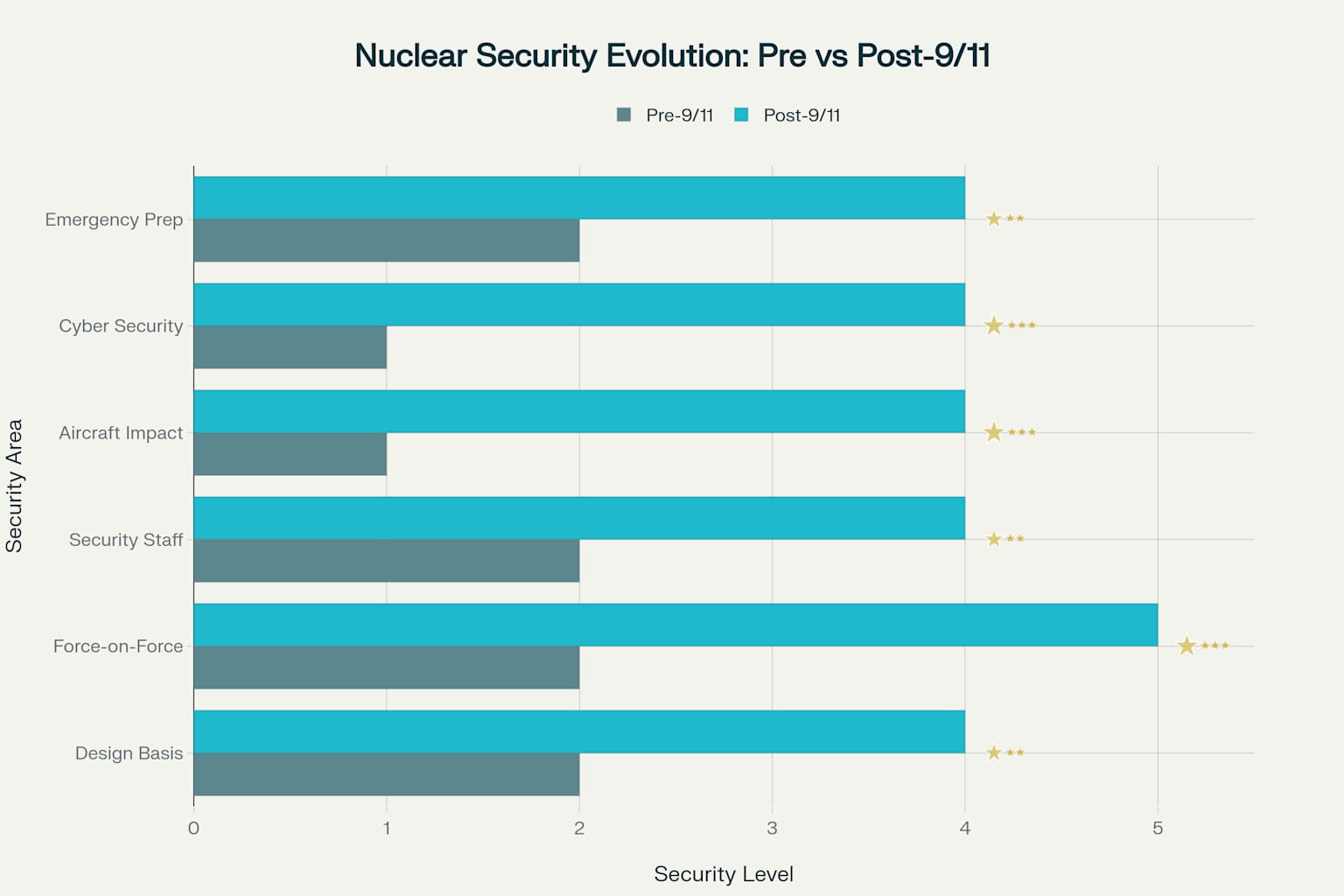
Early nuclear facilities focused primarily on operational safety, with security as a secondary consideration 7. As global security threats evolved, particularly after events like the 9/11 terrorist attacks, the approach to nuclear security underwent a dramatic transformation 38.
What began as basic security measures transformed into comprehensive protection strategies that integrate physical barriers, advanced technology, and highly trained personnel 13. This evolution represents one of the most significant shifts in critical infrastructure protection in modern history 6.
The nuclear industry embraced a “defense-in-depth” philosophy, implementing redundant security layers so that no single failure could compromise the entire facility 9. This approach, borrowed directly from military facility protection, ensures that multiple independent protective measures must be overcome for any threat to succeed 10.
Before the September 11 attacks, nuclear security focused primarily on preventing theft of nuclear materials for weapons 3. Post-9/11, the focus expanded dramatically to include protection against sophisticated terrorist attacks, including potential aircraft impacts and cyber intrusions .
Evolution of Nuclear Security Measures: Before and After 9/11
Defense-in-Depth: The Military Principle at Work
The foundation of nuclear facility security lies in the “defense-in-depth” concept—a military principle that creates multiple, independent, and redundant layers of protection 910. This approach ensures that the failure of any single security element won’t compromise overall facility protection 10.
For civilian nuclear facilities, defense-in-depth spans physical barriers, technology systems, personnel screening, response capabilities, and administrative controls 10. Each layer complements the others, creating a comprehensive security system greater than the sum of its parts 7.
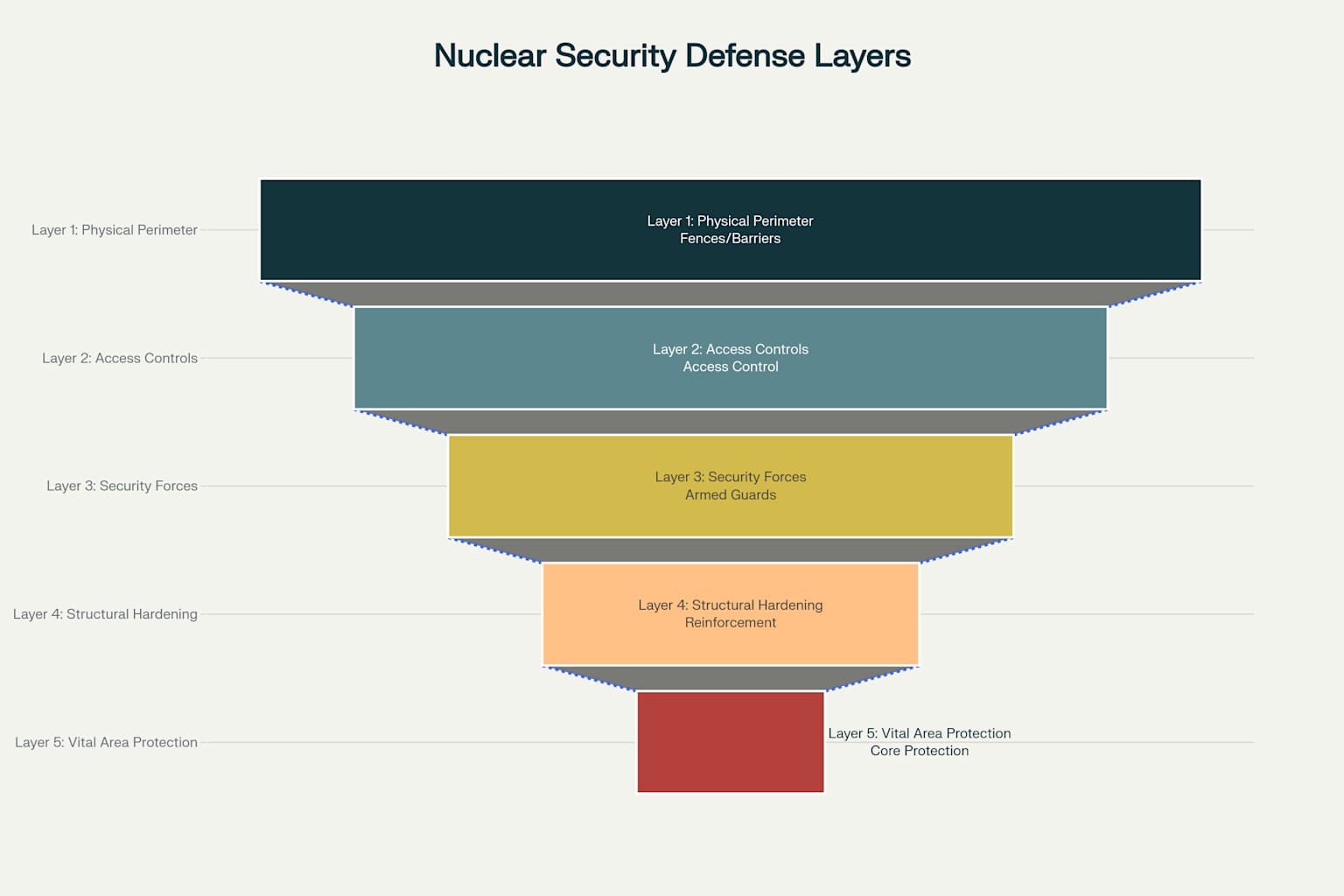
The implementation begins at the facility perimeter and extends inward through increasingly restrictive zones, culminating in the most protected “vital areas” containing critical equipment and materials 1112. This graduated approach optimizes resource allocation while providing maximum protection to the most sensitive areas 4.
Modern nuclear facilities typically employ five distinct defensive layers: physical perimeter barriers, access controls, security personnel, structural hardening, and vital area protection 97. Each layer employs different technologies and approaches, creating diversity that makes the overall system more resilient 10.
Key prevention measures for nuclear facility safety and security, including training, NRC inspections, and fire safety protocols.
The Outer Shield: Physical Perimeter Protection
The first line of defense at any nuclear facility is its perimeter protection system—a sophisticated barrier network designed to control access and detect unauthorized intrusion attempts 12. These systems typically include security fencing, vehicle barriers, intrusion detection systems, and surveillance technologies 613.
Modern nuclear facility perimeters often feature double fence systems with an isolation zone between them, vehicle checkpoints with reinforced barriers, and advanced detection systems 12. The perimeter design must balance operational needs with security requirements, allowing legitimate access while preventing unauthorized entry 13.
Physical barriers at nuclear facilities are specifically engineered to delay adversaries, providing time for security forces to respond to potential threats 14. These barriers include not just fences, but also vehicle denial systems, reinforced entry control points, and natural obstacles incorporated into the security design 13.
Surveillance systems monitor the perimeter continuously, using a combination of video cameras, motion sensors, infrared detection, and often thermal imaging capabilities 6. These technologies create overlapping coverage to eliminate blind spots and ensure complete situational awareness for security personnel 14.

A security gate and wedge barrier system providing access control at a facility’s entrance.
Access Control: The Human Filtering System
Beyond physical barriers, nuclear facilities employ sophisticated access control systems to verify the identity and authorization of all individuals entering protected areas 15. These systems ensure that only properly vetted personnel can access sensitive areas within the facility 12.
Modern access control incorporates multiple verification factors—typically something you have (like an ID badge), something you know (like a PIN), and something you are (like biometric data) 15. This multi-factor approach significantly reduces the risk of unauthorized access through lost credentials or coercion 6.
Personnel screening forms another critical component of the access control system, with all employees and contractors undergoing background checks, psychological evaluations, and ongoing monitoring 15. These measures help identify potential insider threats before they can access sensitive areas or materials 16.
Advanced nuclear facilities now implement zoned access controls, with increasingly stringent verification requirements as personnel move toward more sensitive areas 12. This graduated approach ensures that access to critical systems and materials is limited to only those with legitimate operational need 11.

A specialized security force member rappels during a training exercise, symbolizing the human element in civilian nuclear security.
The Human Element: Security Forces and Response
Trained security personnel represent a crucial layer in nuclear facility protection, providing an adaptive response capability that physical barriers and technology alone cannot offer 6. These specialized forces undergo rigorous training in threat assessment, tactical response, and the unique challenges of nuclear security 17.
Nuclear facility security forces typically operate in multiple tiers, from perimeter patrol officers to specialized response teams equipped for various threat scenarios 817. These personnel are often armed and authorized to use deadly force if necessary to protect critical areas of the facility 14.
Security exercises, including force-on-force drills against mock adversary teams, regularly test both personnel readiness and overall security system effectiveness 3. These realistic training scenarios help identify potential vulnerabilities and ensure response capabilities remain sharp 17.
The integration of security personnel with technology systems creates a far more effective protection system than either element could provide alone 6. Human judgment combined with technological capabilities creates a responsive and adaptive security posture 17.

Armed security personnel conducting a training exercise inside a nuclear facility control room, demonstrating nuclear facility hardening and civilian nuclear security measures.
Structural Fortification: Building in Protection
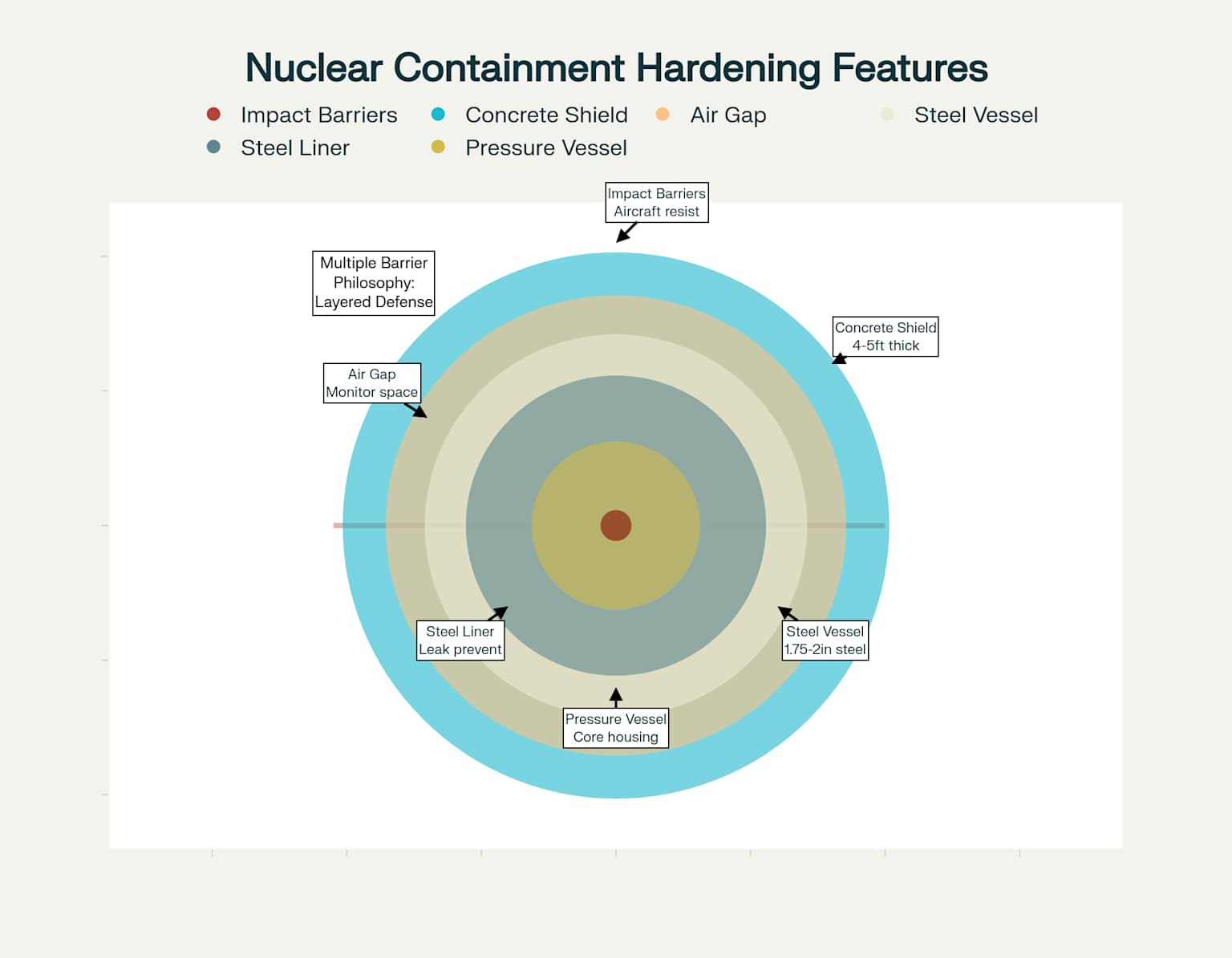
The containment structures at nuclear facilities represent an engineering marvel of protective design, with walls several feet thick made of specially reinforced concrete 18. These massive structures are designed to both contain radiation and resist external forces, including potential deliberate attacks 19.
Modern containment buildings feature multiple protective layers, typically including an outer reinforced concrete shield building and an inner steel containment vessel 18. This layered approach provides redundant protection against both internal accidents and external threats 20.
Post-9/11 assessments led to significant enhancements in structural designs, with newer facilities incorporating specific features to resist aircraft impacts and other severe external threats 2122. These design improvements reflect direct adaptation of military hardening principles to civilian nuclear applications .
The reinforced structures protecting nuclear facilities are engineered to withstand extreme events including tornadoes, hurricanes, earthquakes, floods, and explosions 1819. This robust design philosophy creates facilities that are inherently resistant to both natural disasters and deliberate attacks .
Key Hardening Features of Nuclear Containment Buildings
Inside the Shield: Vital Area Protection
At the core of nuclear facility protection lies the concept of “vital areas”—spaces containing equipment or materials whose compromise could lead to unacceptable consequences 11. These areas receive the highest level of protection through multiple overlapping security measures 12.
Vital areas typically include the reactor control room, central alarm stations, emergency power systems, and locations housing nuclear materials 11. Access to these areas is strictly controlled, often requiring multiple authorization factors and continuous monitoring 12.
Security measures for vital areas often include hardened doors, mantrap entry systems, continuous surveillance, and intrusion detection systems with immediate alarm capabilities 611. Many facilities also employ the “two-person rule” within vital areas, requiring at least two authorized individuals to be present at all times 15.
The protection of vital areas represents the culmination of the defense-in-depth approach, with all previous security layers working together to prevent adversaries from ever reaching these critical spaces 119. This comprehensive protection strategy creates extraordinary difficulty for any attempt to compromise essential systems 14.
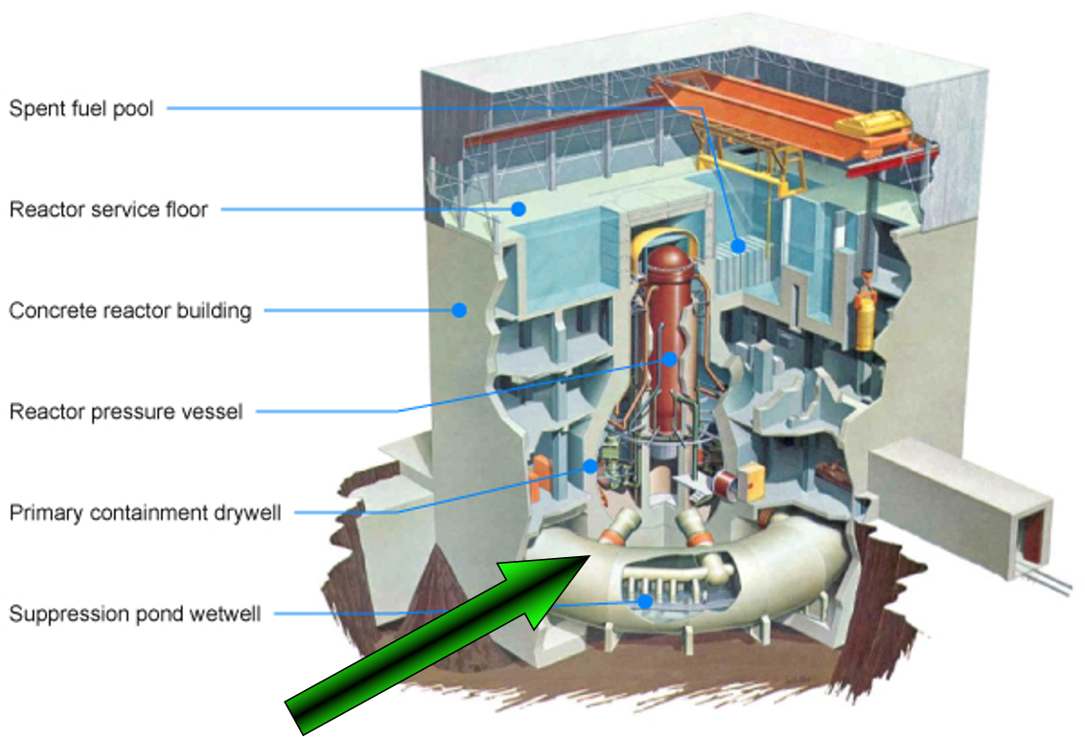
Cutaway diagram of a nuclear reactor building illustrating key containment and structural components.
Cyber Protection: The Digital Fortress
Modern nuclear facilities face not just physical threats but also sophisticated cyber attacks that could potentially compromise critical control systems 23. Protecting against these digital threats requires specialized security measures adapted from both military and information security domains 24.
Nuclear cyber protection typically employs an “air gap” approach where critical safety and control systems are physically isolated from external networks 23. This separation creates a significant barrier to remote cyber attacks, though it must be supported by strict protocols for any data transfer across this gap 25.
Defense-in-depth applies equally to cyber security, with multiple independent protective layers including firewalls, intrusion detection systems, encryption, and access controls 1624. These overlapping defenses ensure that no single security failure can compromise critical systems 25.
Personnel training represents a crucial element of cyber protection, as human error or insider actions remain significant potential vulnerability points 15. Regular security awareness training, access restrictions, and monitoring help mitigate these risks 16.

Military personnel in tactical gear monitor complex systems in what appears to be a nuclear facility control room or training simulator.
Personnel Reliability: Countering the Insider Threat
One of the most challenging aspects of nuclear security is addressing the potential for insider threats—authorized personnel who might deliberately compromise security 15. Comprehensive personnel reliability programs have been developed to address this unique vulnerability 15.
These programs begin with thorough background investigations before employment and continue with ongoing monitoring throughout an individual’s access to sensitive areas or materials 15. Regular re-evaluations ensure that changes in an individual’s circumstances are identified and assessed 15.
Behavioral observation programs train supervisors and colleagues to recognize potential warning signs such as unusual behavior, financial difficulties, or unexplained absences 15. This continuous monitoring creates a human sensor network that can identify potential concerns before they lead to security incidents 15.
Many facilities implement the “two-person rule” for sensitive operations, requiring at least two qualified individuals to be present during any activity involving critical systems or materials 15. This approach ensures that no individual can act alone to compromise security 16.

Cutaway diagram of a nuclear reactor containment building showing key structural and operational components.
Regulatory Framework: Standards and Oversight
Nuclear facility security operates within a comprehensive regulatory framework that establishes minimum requirements and provides ongoing oversight 4. These regulations continually evolve to address emerging threats and incorporate lessons learned from security assessments 3.
In the United States, the Nuclear Regulatory Commission (NRC) establishes and enforces security regulations, conducting regular inspections and requiring specific performance standards 3. Similar regulatory bodies exist in other nations with civilian nuclear programs, often following international guidelines 4.
The International Atomic Energy Agency (IAEA) provides globally recognized security recommendations through publications like INFCIRC/225/Revision 5, establishing consistent standards across national boundaries 4. These guidelines help ensure that nuclear facilities worldwide maintain appropriate security levels 4.
Regulatory requirements typically include specific provisions for physical protection systems, access controls, security personnel, cyber security, and emergency response capabilities 3. These comprehensive standards create a baseline of protection that all facilities must meet or exceed 4.
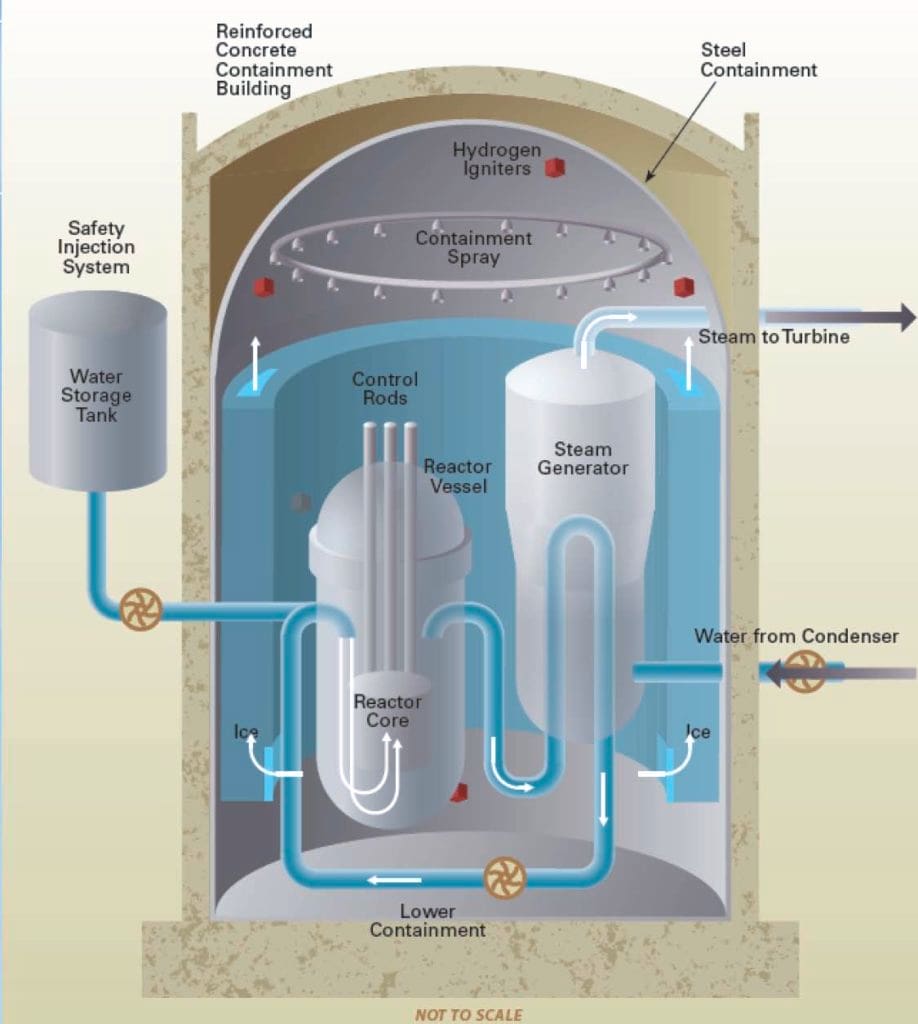
Diagram of a nuclear power plant containment building illustrating its layered structure and key safety systems.
The Future of Nuclear Hardening: Evolving Threats and Solutions
As security threats continue to evolve, so too must the approaches to nuclear facility hardening 16. Emerging challenges include increasingly sophisticated cyber attacks, advanced drone technologies, and the potential for coordinated physical and digital attacks 2616.
Next-generation nuclear facilities are incorporating security considerations from the earliest design phases, creating integrated protection rather than adding security measures to existing structures 27. This “security by design” approach represents a significant advancement in nuclear facility hardening 6.
Advanced technologies including artificial intelligence for threat detection, adaptive security systems, and enhanced sensor networks are being deployed at modern nuclear facilities 616. These innovations provide more effective protection with optimized resource allocation 23.
International cooperation on nuclear security continues to strengthen, with information sharing and joint training exercises becoming increasingly common 24. This collaborative approach helps ensure that best practices and threat intelligence benefit all nuclear facilities worldwide 4.
Conclusion: The Ongoing Security Evolution
The application of military hardening principles to civilian nuclear facilities has created some of the world’s most secure industrial installations . This comprehensive approach to protection demonstrates how critical infrastructure security can effectively adapt concepts from defense facilities 28.
The defense-in-depth philosophy remains the cornerstone of nuclear security, creating multiple independent protective layers that work together to ensure facility protection 910. This redundant approach minimizes vulnerabilities and maximizes overall security effectiveness 7.
As security threats continue to evolve, so too will the approaches to nuclear facility hardening, incorporating new technologies and methodologies to address emerging challenges 1624. This constant evolution ensures that protection measures remain effective against changing threat landscapes 3.
The balance between operational needs and security requirements remains an ongoing challenge, requiring thoughtful integration of protection measures with facility functionality 6. This integration ensures that security enhances rather than hinders the vital energy production mission of nuclear facilities 3.
The successful hardening of civilian nuclear facilities demonstrates how security principles can be effectively transferred across domains, creating robust protection for critical infrastructure that serves essential societal needs 28. This transfer of knowledge continues to strengthen security across sectors 6.
Footnotes
-
https://www.eesi.org/files/Principles_for_Safeguarding_Nuclear_Waste_at_Reactors.pdf ↩ ↩2
-
https://world-nuclear.org/information-library/safety-and-security/security/security-of-nuclear-facilities-and-material ↩ ↩2
-
https://www.nrc.gov/reading-rm/doc-collections/fact-sheets/security-enhancements.html ↩ ↩2 ↩3 ↩4 ↩5 ↩6 ↩7 ↩8 ↩9 ↩10 ↩11
-
https://www-pub.iaea.org/MTCD/Publications/PDF/Pub1481_web.pdf ↩ ↩2 ↩3 ↩4 ↩5 ↩6 ↩7 ↩8
-
https://www.nirs.org/campaigns/dont-waste-america/hardened-site-storage/ ↩
-
https://www.nei.org/resources/fact-sheets/nuclear-plant-security-and-access-control ↩ ↩2 ↩3 ↩4 ↩5 ↩6 ↩7 ↩8 ↩9 ↩10 ↩11 ↩12
-
https://www.neimagazine.com/advanced-reactorsfusion/the-real-truth-about-nuclear-power-plant-security/ ↩ ↩2 ↩3 ↩4
-
https://www.nrc.gov/security/faq-security-assess-nuc-pwr-plants.html ↩ ↩2
-
https://www.nrc.gov/docs/ML1610/ML16104A071.pdf ↩ ↩2 ↩3 ↩4 ↩5 ↩6
-
https://test.ucsaction.org/sites/default/files/2019-09/20011204-ucs-backgrounder-security-illustrated.pdf ↩ ↩2 ↩3 ↩4 ↩5 ↩6 ↩7
-
https://www.covasecuritygates.com/2025/05/28/the-future-of-secure-perimeter-protection-for-nuclear-power-plants/ ↩ ↩2 ↩3
-
https://www.nrc.gov/security/domestic/phys-protect.html ↩ ↩2 ↩3 ↩4
-
https://www.numberanalytics.com/blog/safeguarding-nuclear-facilities-from-insider-threats ↩ ↩2 ↩3 ↩4 ↩5 ↩6 ↩7 ↩8 ↩9 ↩10 ↩11 ↩12
-
https://www.nti.org/about/programs-projects/project/addressing-cyber-nuclear-security-threats/ ↩ ↩2 ↩3 ↩4 ↩5 ↩6 ↩7 ↩8
-
https://world-nuclear.org/information-library/safety-and-security/safety-of-plants/safety-of-nuclear-power-reactors ↩ ↩2
-
https://ecolo.org/documents/documents_in_english/AirplaneImpactAnalyses.pdf ↩
-
https://repository.lib.ncsu.edu/server/api/core/bitstreams/3a9582bd-05d0-4de8-8aad-8902cf9d322d/content ↩
-
https://www.nei.org/fundamentals/safety/cybersecurity ↩ ↩2 ↩3
-
https://www.cisa.gov/sites/default/files/publications/Nuclear_Sector_Cybersecurity_Framework_Implementation_Guidance_FINAL_508.pdf ↩ ↩2 ↩3 ↩4
-
https://www.indeavor.com/blog/guardians-of-the-reactor-the-crucial-role-of-cybersecurity-in-nuclear-operations/ ↩ ↩2
-
https://www.defenseadvancement.com/feature/countering-drone-incursions-at-nuclear-sites-with-rf-cyber-takeover-technology/ ↩
-
https://en.wikipedia.org/wiki/Defense_in_depth_(nuclear_engineering) ↩ ↩2